Secret Management
UPDATE: The Ash Console open beta has ended. Looking to launch your Avalanche L1? See our latest Ash Managed L1s offer announcement!
Secrets are used at different steps of an Avalanche L1 deployment through the Ash Console.
Types of secrets
There are several types of secrets, each with a different purpose. See Secret for more information.
List secrets
- Using the Ash Console
- Using the Ash CLI
- Using the Ash Console API
To list the secrets in the Ash Console, navigate to the Secrets tab:
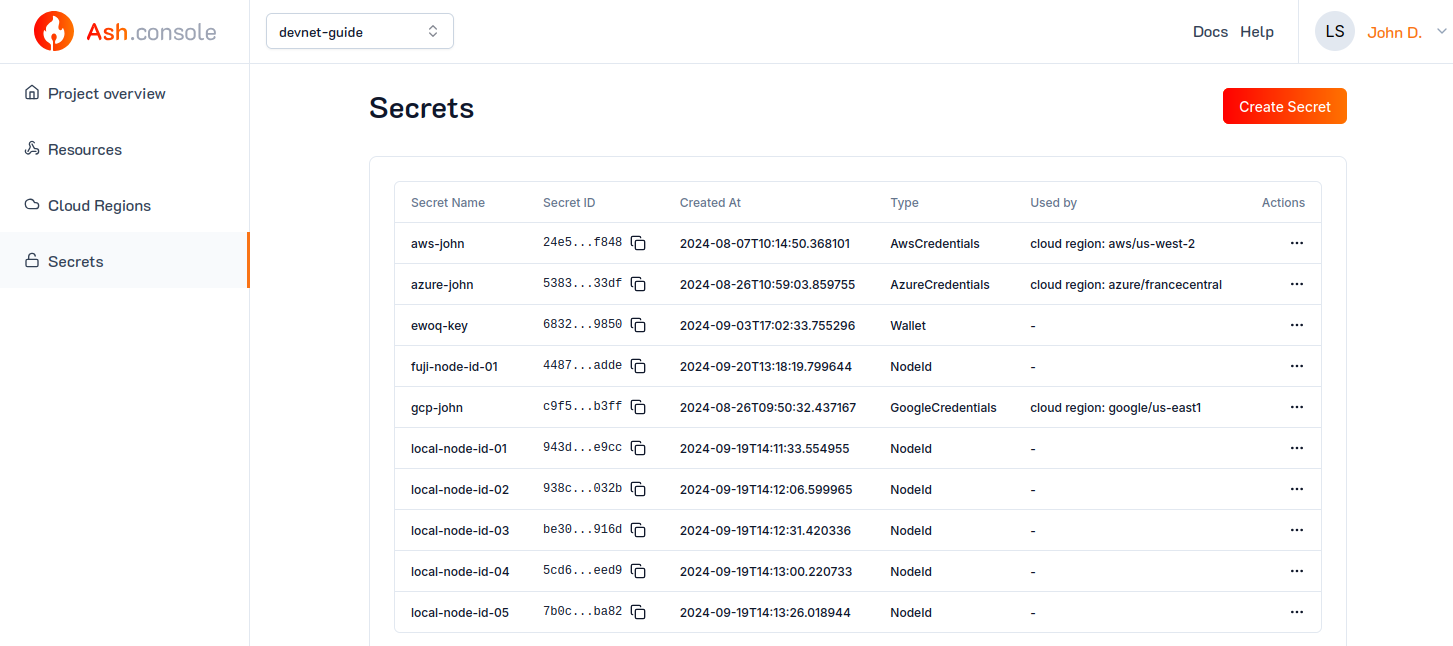
The Ash CLI displays information in a table format by default. To get a more detailed output (or for scripting), use the --json flag.
To list secrets you have access to, run:
ash console secret list
+-------------+-----------+------+------------+---------+
| Secret name | Secret ID | Type | Created at | Used by |
+=============+===========+======+============+=========+
+-------------+-----------+------+------------+---------+
See Authentication for more information on how to get an access token.
The secret API endpoint is /secrets.:
curl https://api.console.ash.center/secrets \
-H "Authorization: Bearer ${access_token}"
[]
Create a secret
A secret sensitive values can never be retrieved from the Ash Console! Make sure to keep a copy in a safe place.
- Using the Ash Console
- Using the Ash CLI
- Using the Ash Console API
To create a secret, navigate to the Secrets tab, click on the Create secret button, and provide the required secret properties:
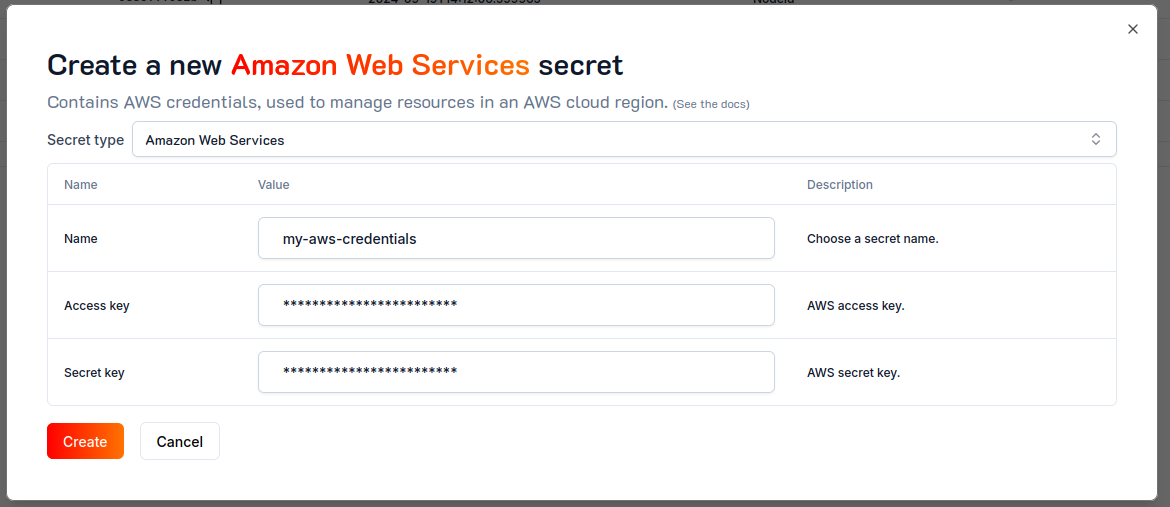
To create a new secret, use the create secret command and provide the required secret properties as JSON:
ash console secret create '{name: my-secret, secretType: generic, content: "***"}'
Secret created successfully!
+-------------+-------------+---------+------------------+---------+
| Secret name | Secret ID | Type | Created at | Used by |
+=============+=============+=========+==================+=========+
| my-secret | 5a46...fba3 | Generic | 2024-04-04T15:27 | 0 |
+-------------+-------------+---------+------------------+---------+
To create a new secret, you have to send a POST request with the required secret properties as JSON:
curl -X POST https://api.console.ash.center/secrets \
-H "Authorization: Bearer ${access_token}" \
-H "Content-Type: application/json" \
-d '{"name": "my-secret", "secretType": "generic", "content": "***"}'
{
"id": "6c7f3c7a-7e15-4359-b7cf-3eaacb1938c2",
"ownerId": "4d4dee2d-e943-432c-91ee-678975615caa",
"name": "my-secret",
"secretType": "generic",
"created": "2024-04-04T15:28:36.954694",
"usedBy": {},
"content": "**********"
}
Update a secret
You can also provide the secret name instead of its ID.
- Using the Ash Console
- Using the Ash CLI
- Using the Ash Console API
To update a secret, navigate to the Secrets tab, click on a secret. Update the needed properties and :
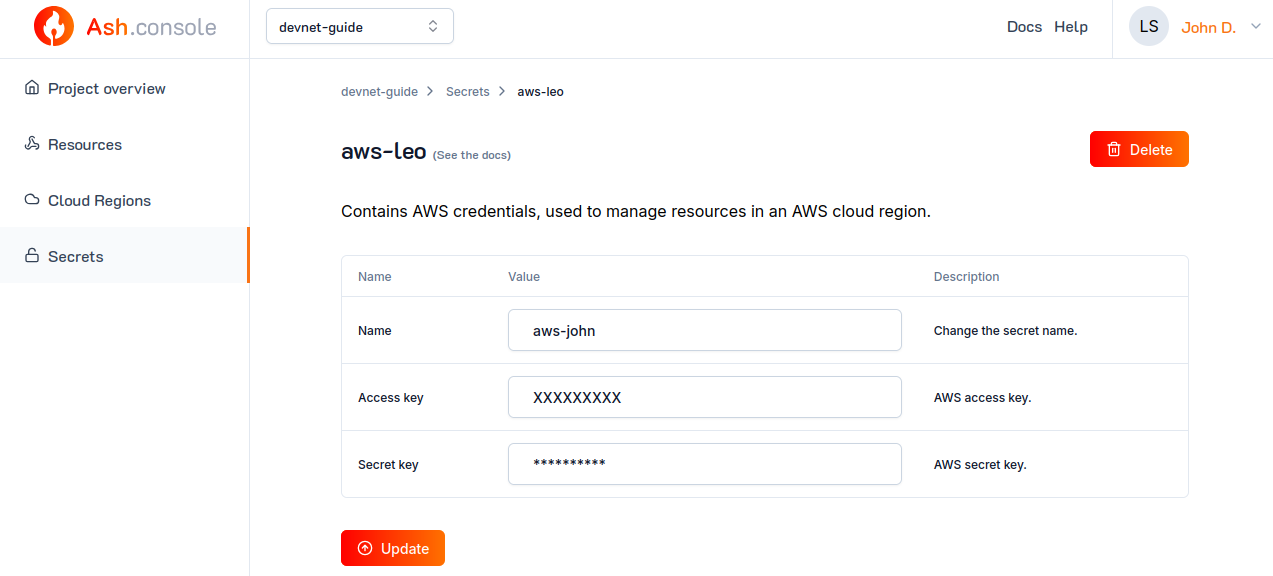
The properties that can be updated depend on the secret type. For example, you can update a generic secret's name and content:
ash console secret update 6c7f3c7a-7e15-4359-b7cf-3eaacb1938c2 '{name: my-secret-updated, content: "****"}'
Secret updated successfully!
+-------------------+-------------+---------+------------------+---------+
| Secret name | Secret ID | Type | Created at | Used by |
+===================+=============+=========+==================+=========+
| my-secret-updated | 6c7f...38c2 | Generic | 2024-04-04T15:28 | 0 |
+-------------------+-------------+---------+------------------+---------+
The properties that can be updated depend on the secret type. For example, you can update a generic secret's name and content by sending a PATCH to the secrets/${secretId} endpoint:
curl -X PATCH https://api.console.ash.center/secrets/6c7f3c7a-7e15-4359-b7cf-3eaacb1938c2 \
-H "Authorization: Bearer ${access_token}" \
-H "Content-Type: application/json" \
-d '{"name": "my-secret-updated", "content": "****"}'
{
"id": "6c7f3c7a-7e15-4359-b7cf-3eaacb1938c2",
"ownerId": "4d4dee2d-e943-432c-91ee-678975615caa",
"name": "my-secret-updated",
"secretType": "generic",
"created": "2024-04-04T15:28:36.954694",
"usedBy": {},
"content": "**********"
}
Delete a secret
Deleting a secret is not allowed if it used by another entity.
- Using the Ash Console
- Using the Ash CLI
- Using the Ash Console API
To delete a secret, navigate to the Secrets tab, click on the ... and then Delete button of secret:
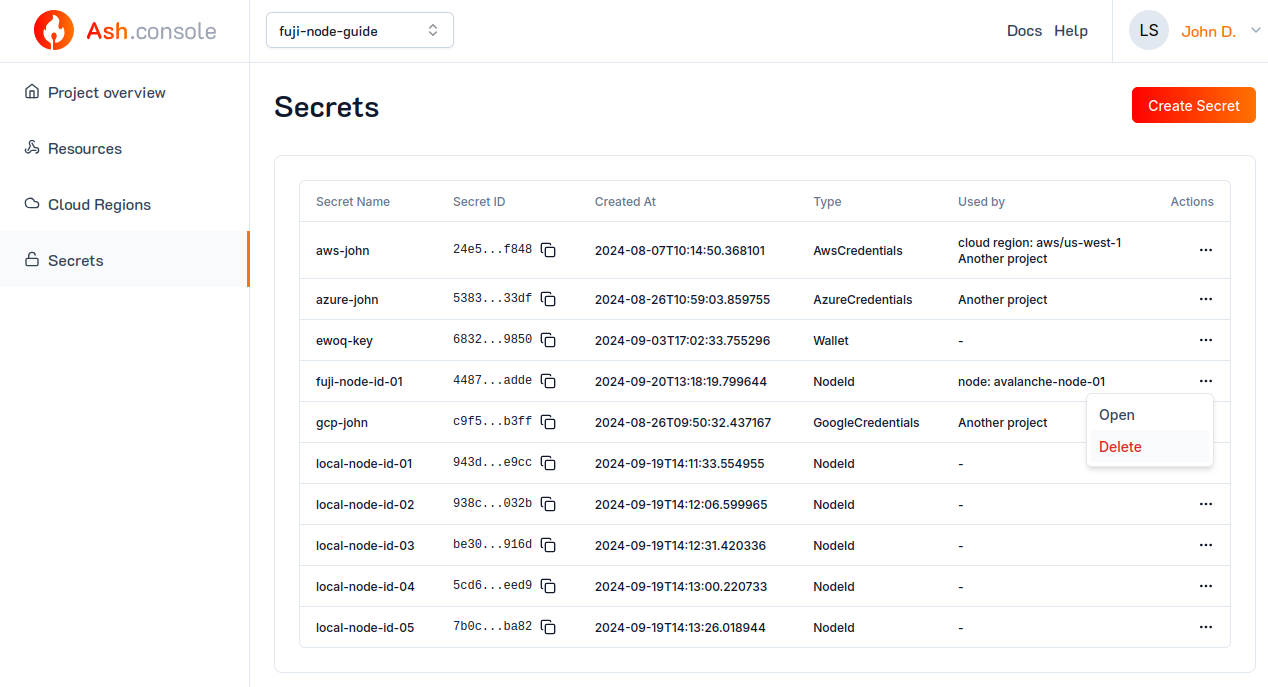
The CLI will ask for confirmation before deleting the secret. To skip the confirmation, use the --yes flag.
ash console secret delete my-secret-updated
+-------------------+-------------+---------+------------------+---------+
| Secret name | Secret ID | Type | Created at | Used by |
+===================+=============+=========+==================+=========+
| my-secret-updated | 6c7f...38c2 | Generic | 2024-04-04T15:28 | 0 |
+-------------------+-------------+---------+------------------+---------+
> Are you sure you want to delete this secret? Yes
Secret deleted successfully!
curl -X DELETE https://api.console.ash.center/secrets/my-secret-updated \
-H "Authorization: Bearer ${access_token}"
{
"id": "6c7f3c7a-7e15-4359-b7cf-3eaacb1938c2",
"ownerId": "4d4dee2d-e943-432c-91ee-678975615caa",
"name": "my-secret-updated",
"secretType": "generic",
"created": "2024-04-04T15:28:36.954694",
"usedBy": {},
"content": "**********"
}